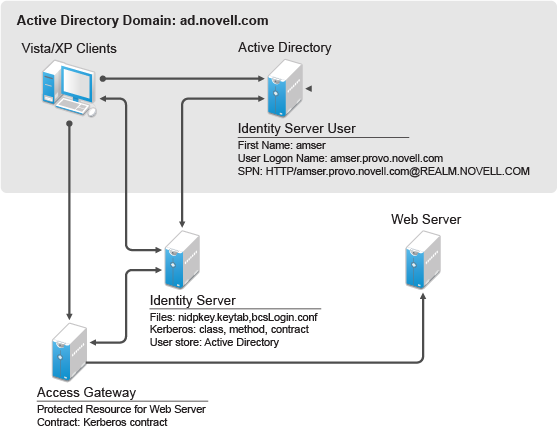
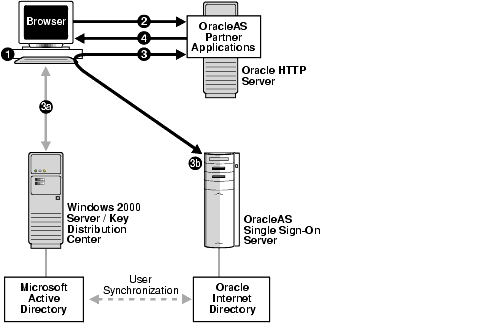
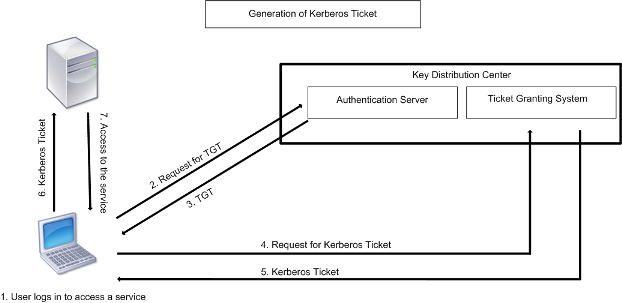
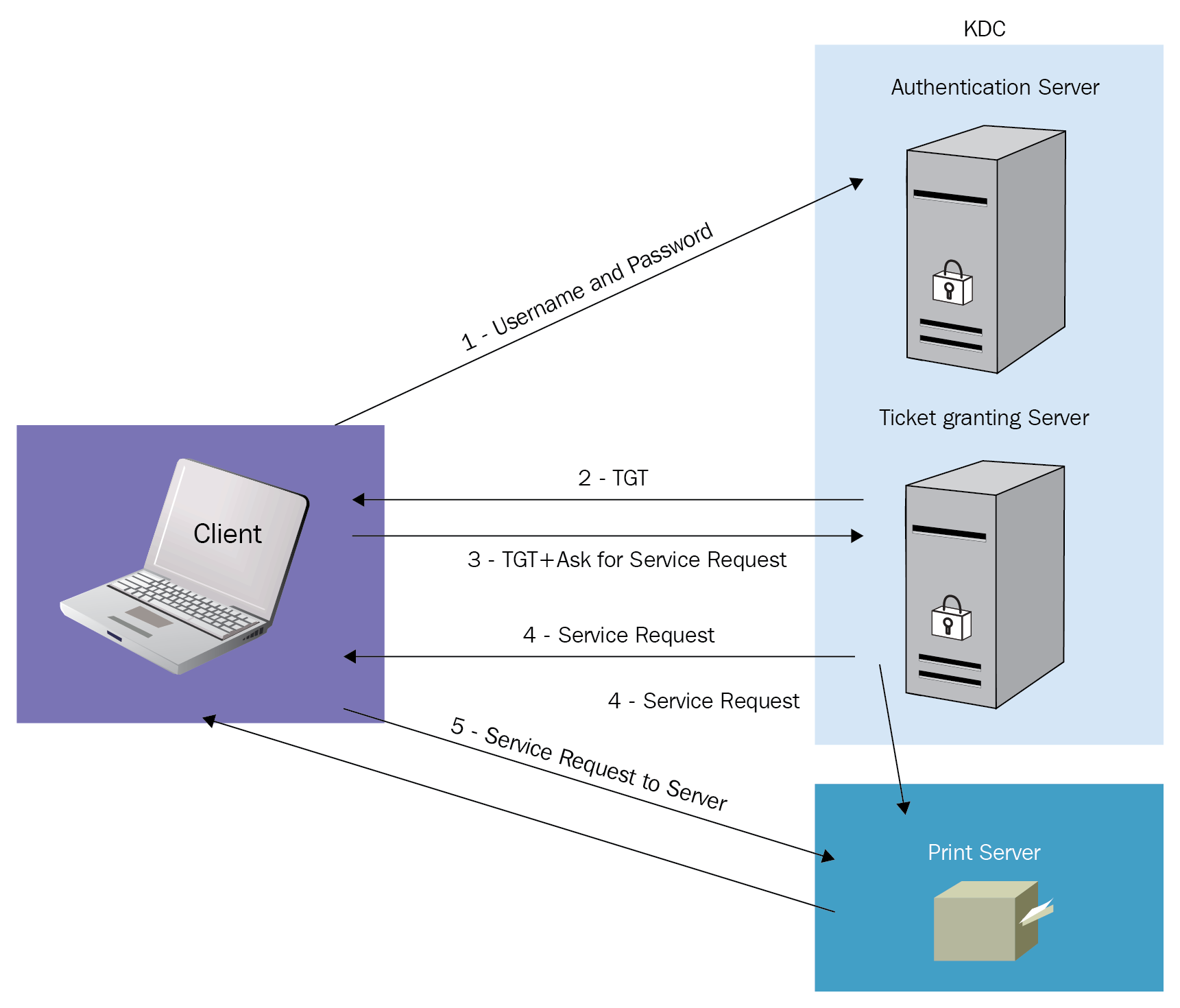
Security Thoughts: Leveraging NTLM Hashes using Kerberos RC4-HMAC encryption (AKA Aorato's Active Directory Vulnerability) - The things that are better left unspoken
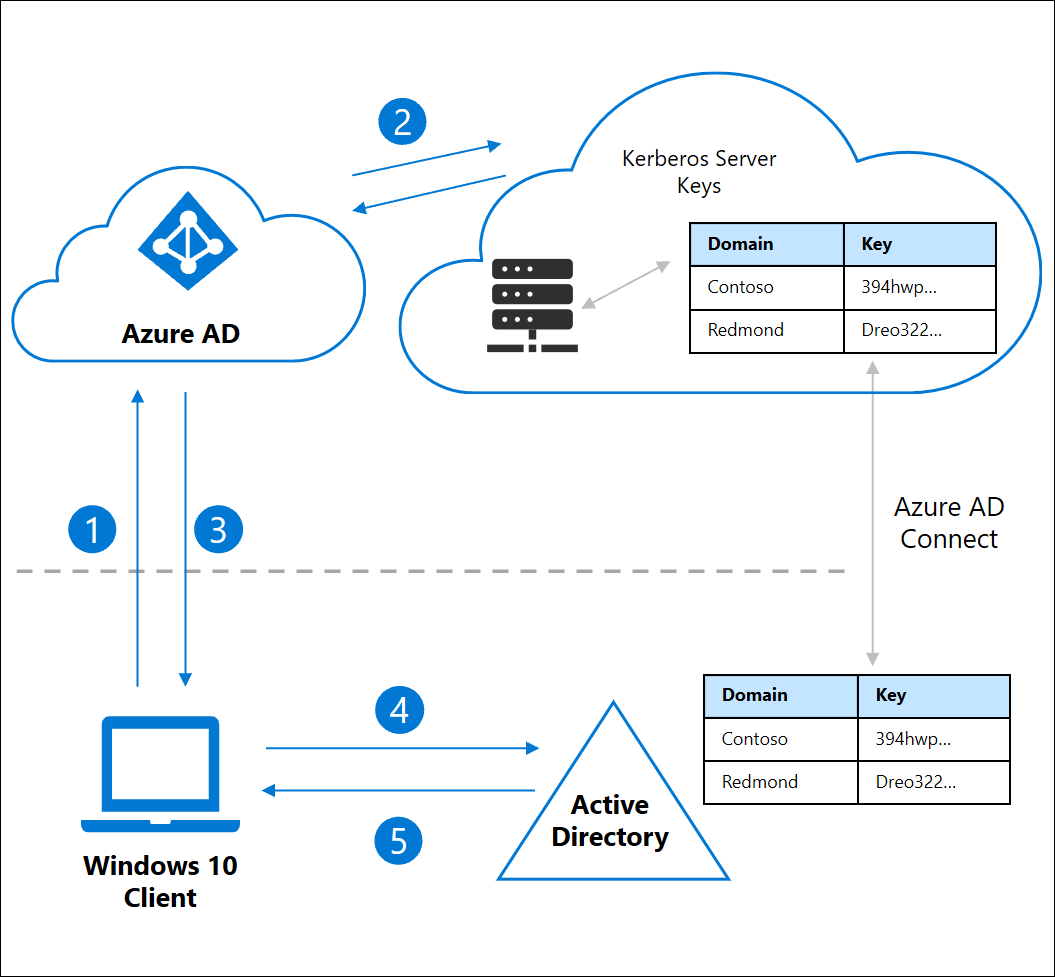
Accesso con chiave di sicurezza senza password alle risorse locali - Microsoft Entra | Microsoft Learn

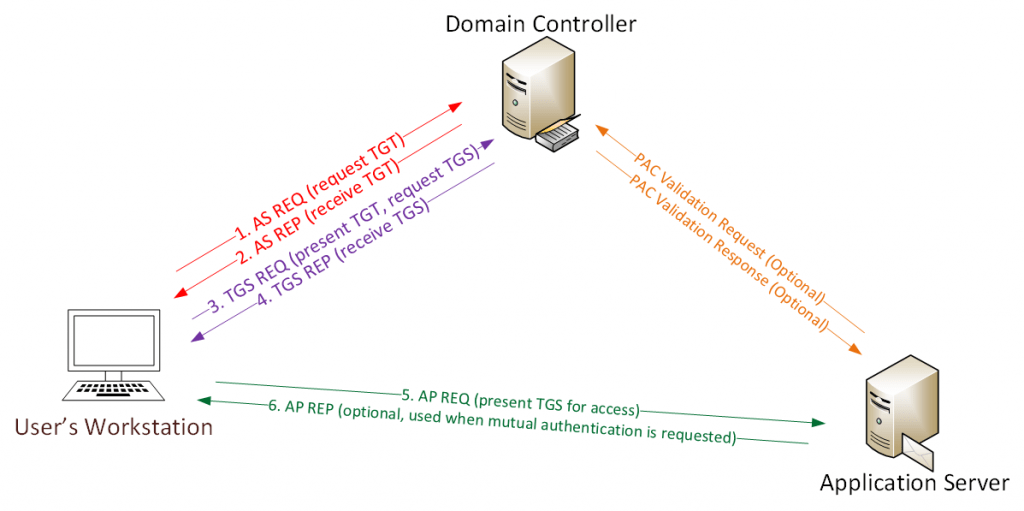
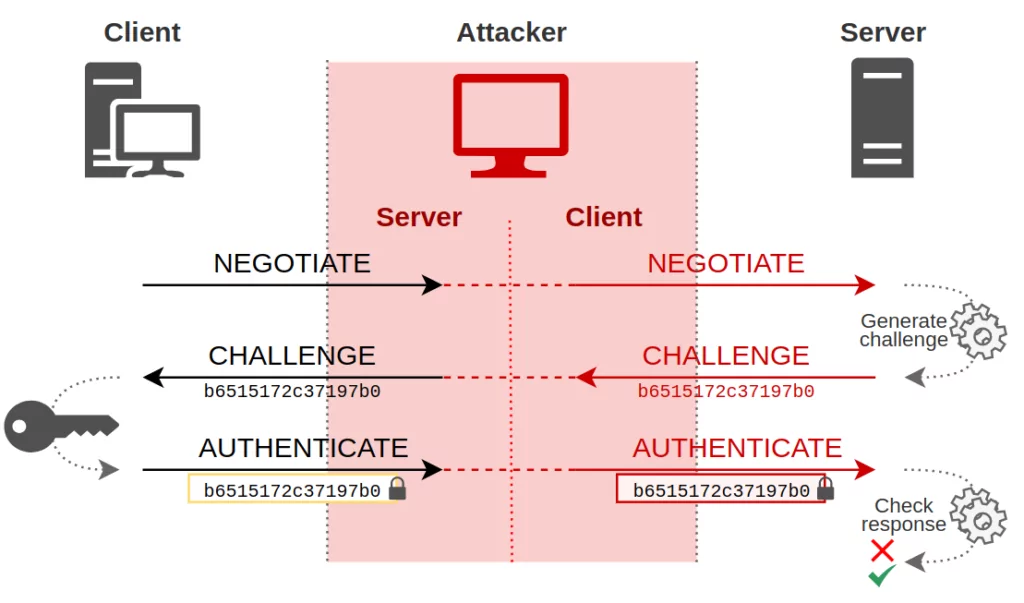
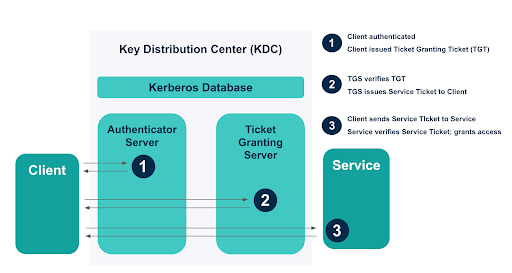
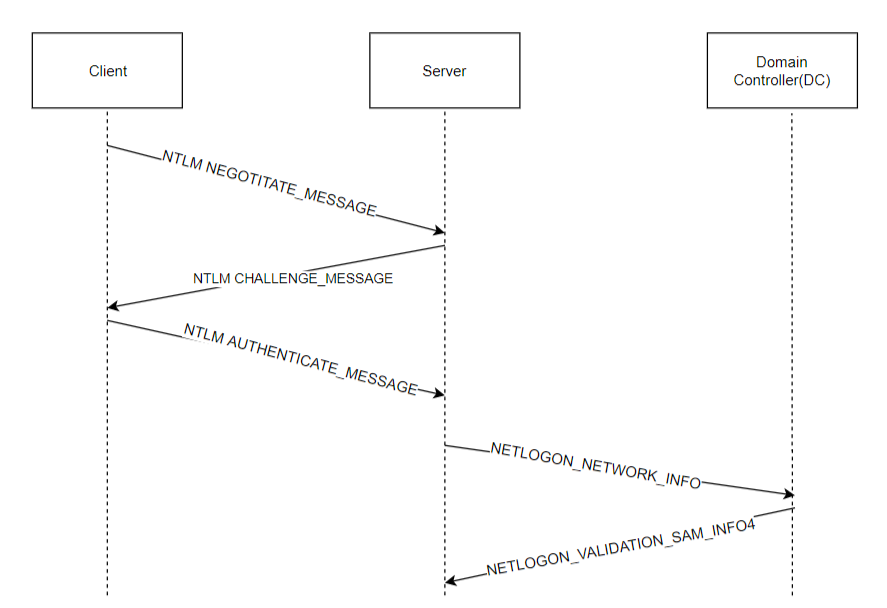
NTLM vs Kerberos: Understanding Authentication in Windows/Active Directory | by Jai Gupta | InfoSec Write-ups

NTLM vs Kerberos: Understanding Authentication in Windows/Active Directory | by Jai Gupta | InfoSec Write-ups
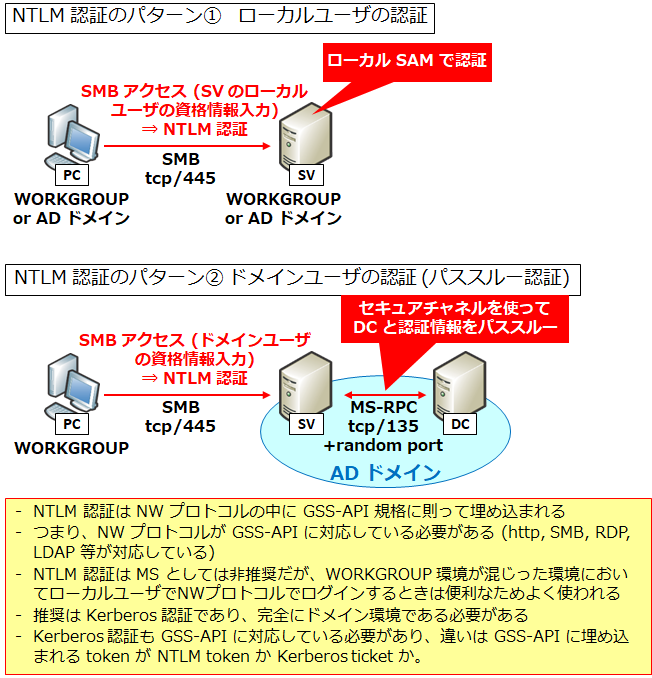
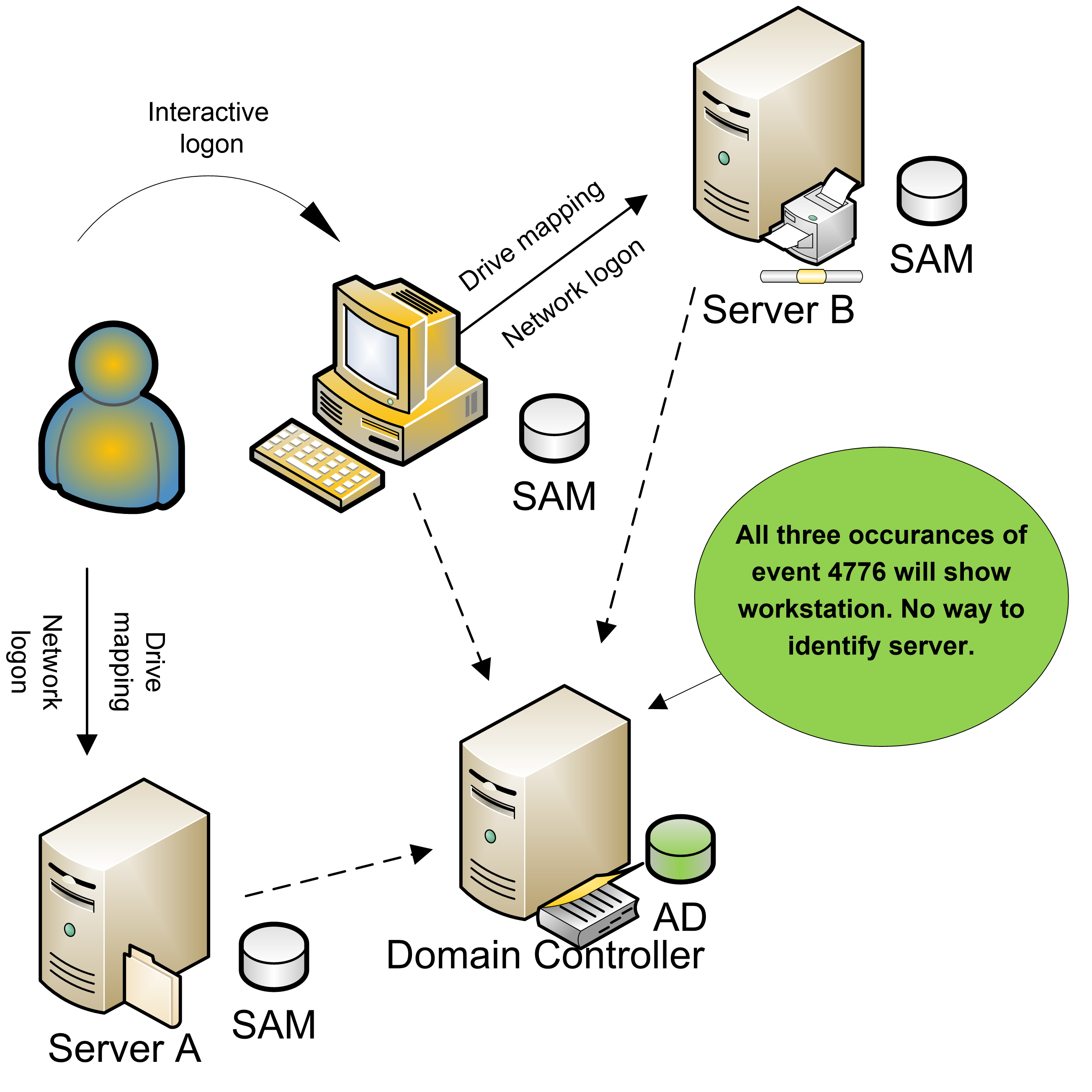
Understanding how NTLM Credentials are validated, with ProxySG, to explain the root cause of Frequent User account lockout.