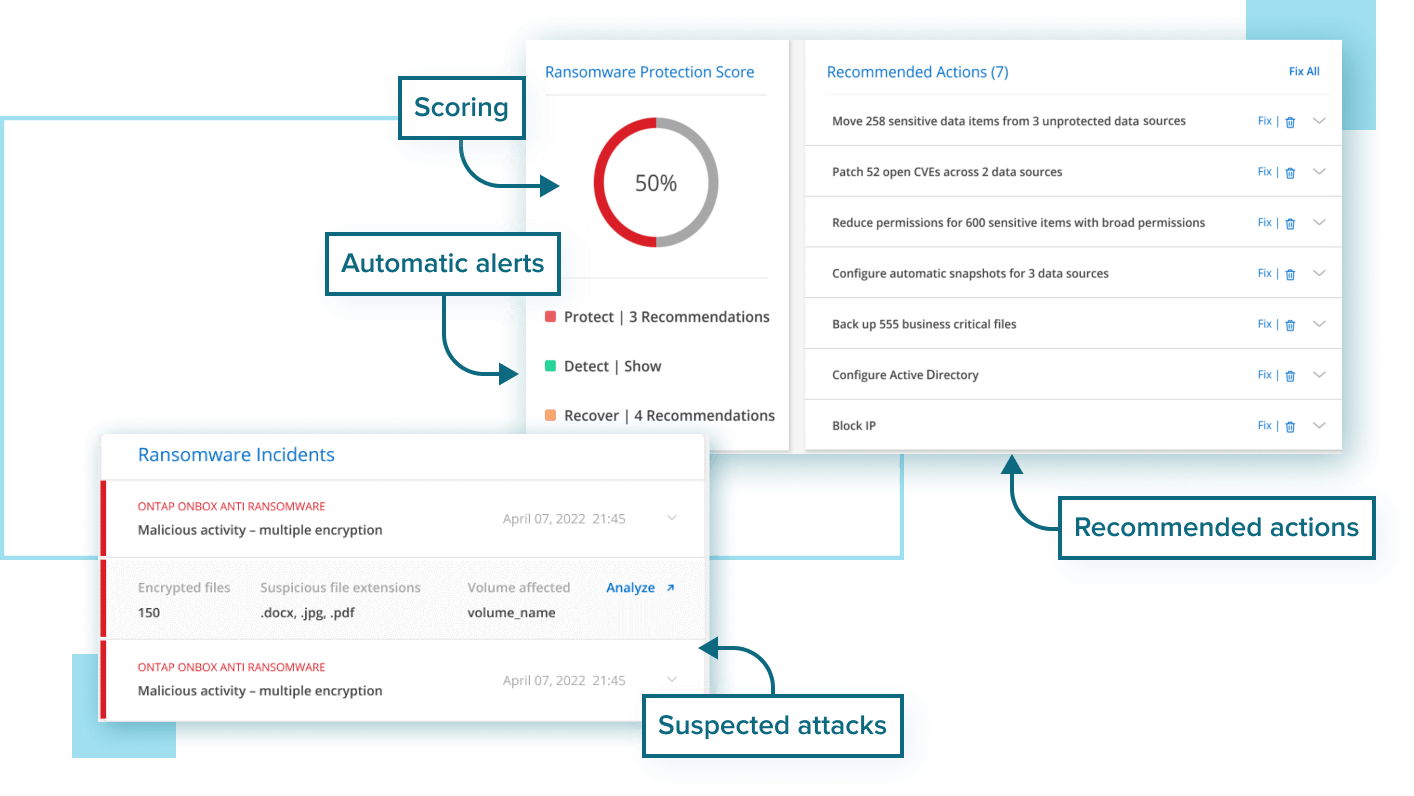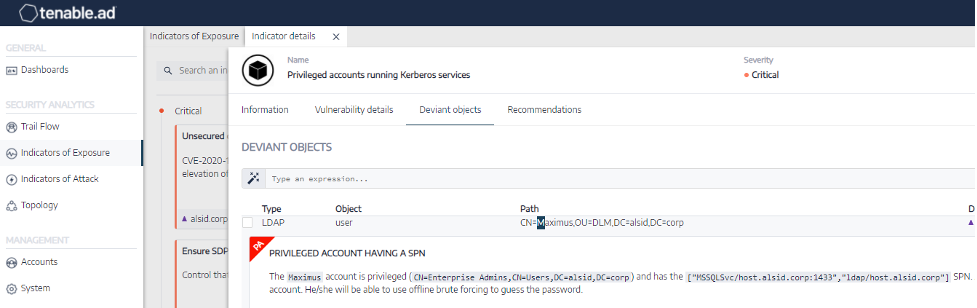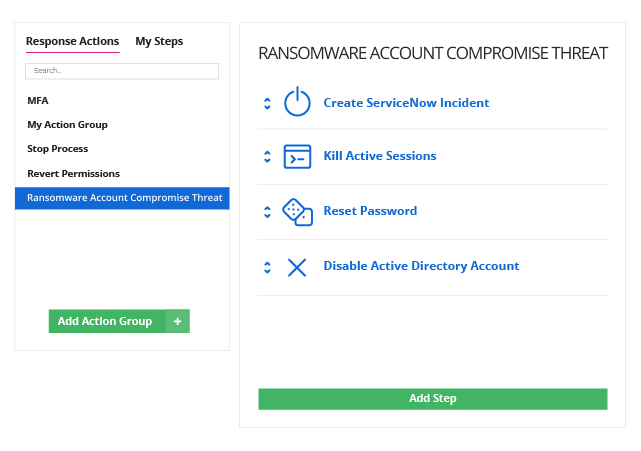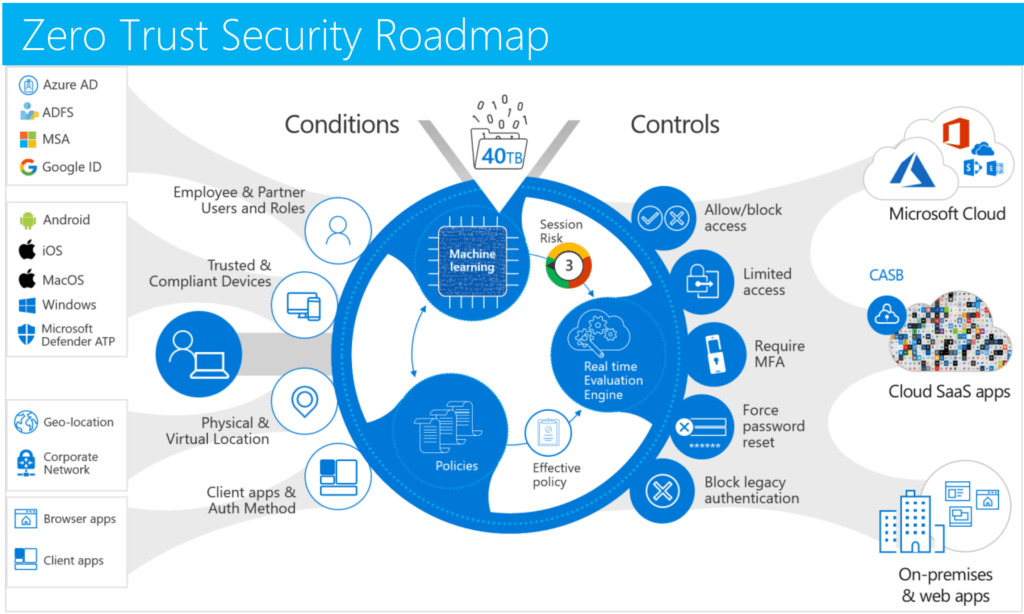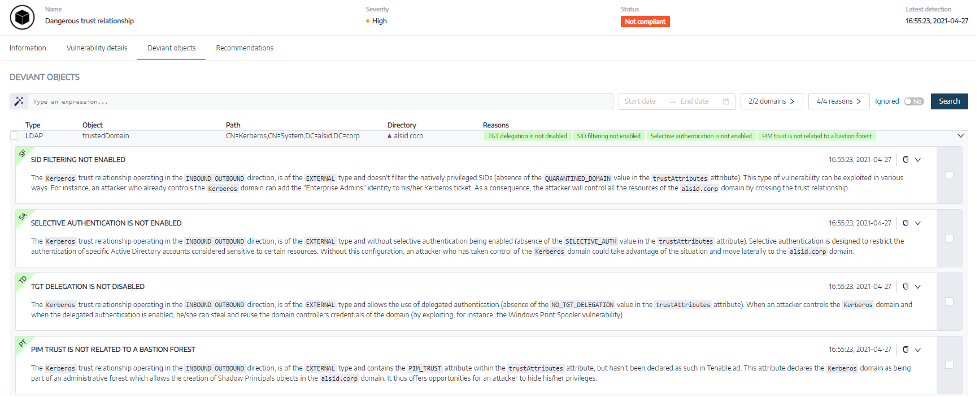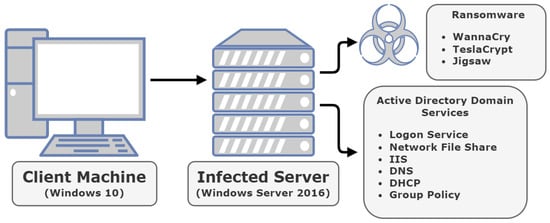
Sensors | Free Full-Text | Ransomware: Analysing the Impact on Windows Active Directory Domain Services

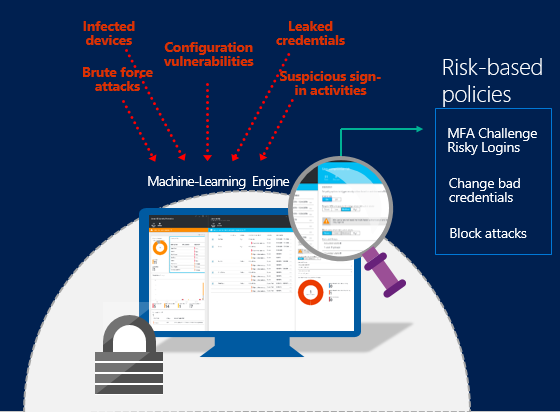
Protection Against Targeted Active Directory Ransomware | by Venu Vissamsetty | AttivoTechBlogs | Medium
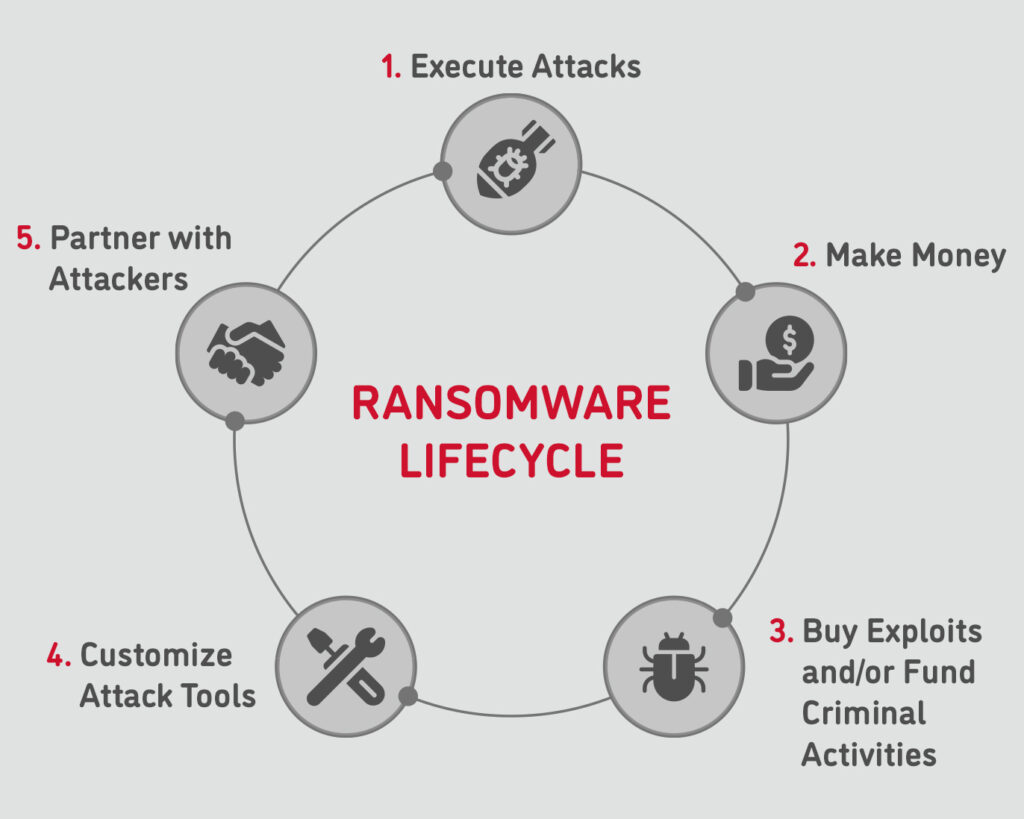
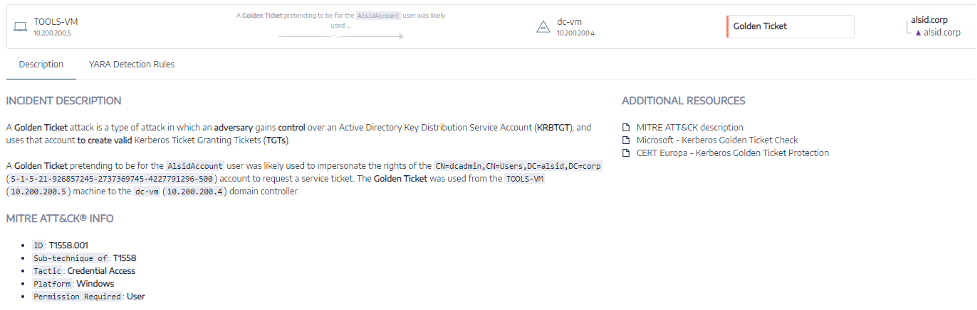
Stories from the Trenches: How to Protect Active Directory against Ransomware Attacks - This Week Health