
Inside Microsoft 365 Defender: Attack modeling for finding and stopping lateral movement | Microsoft Security Blog
Death from Above: Lateral Movement from Azure to On-Prem AD | by Andy Robbins | Posts By SpecterOps Team Members
GitHub - infosecn1nja/AD-Attack-Defense: Attack and defend active directory using modern post exploitation adversary tradecraft activity

How to stop lateral movement attacks using Microsoft 365 DefenderHow to prevent lateral movement attacks using Microsoft 365 Defender | Microsoft Security Blog

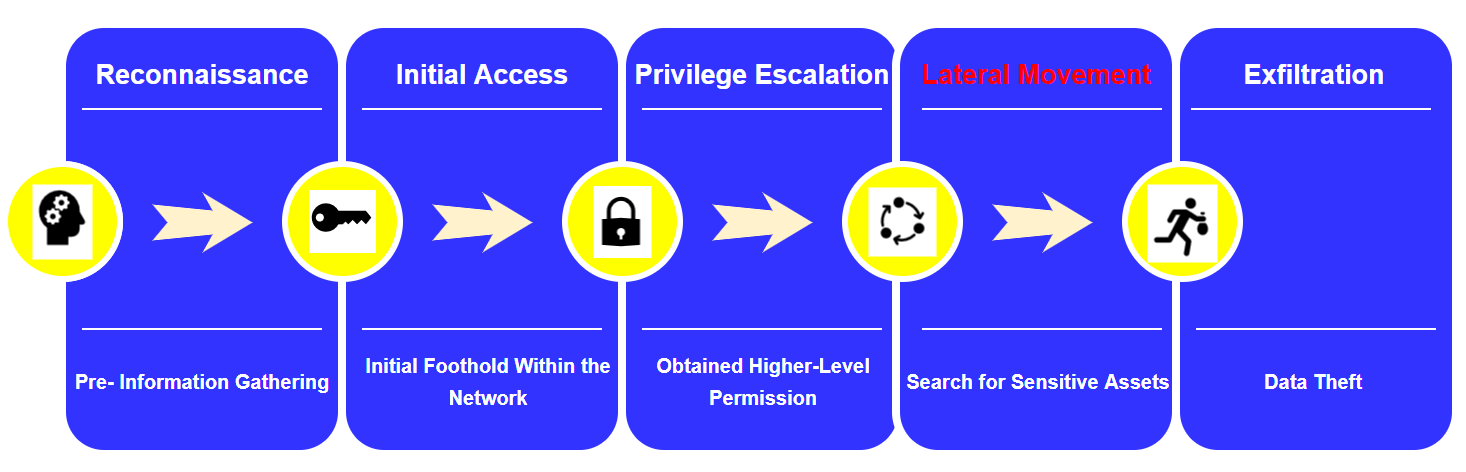
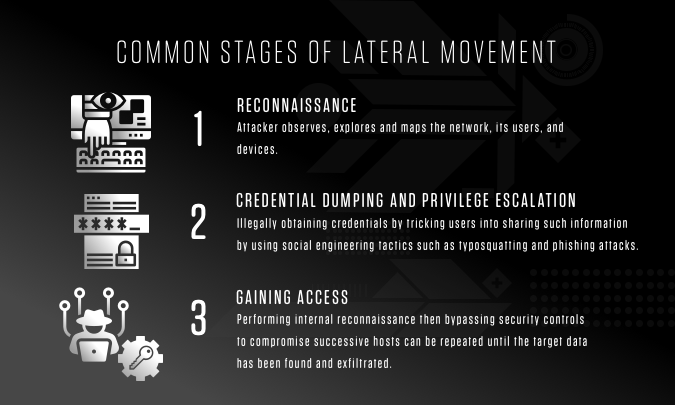


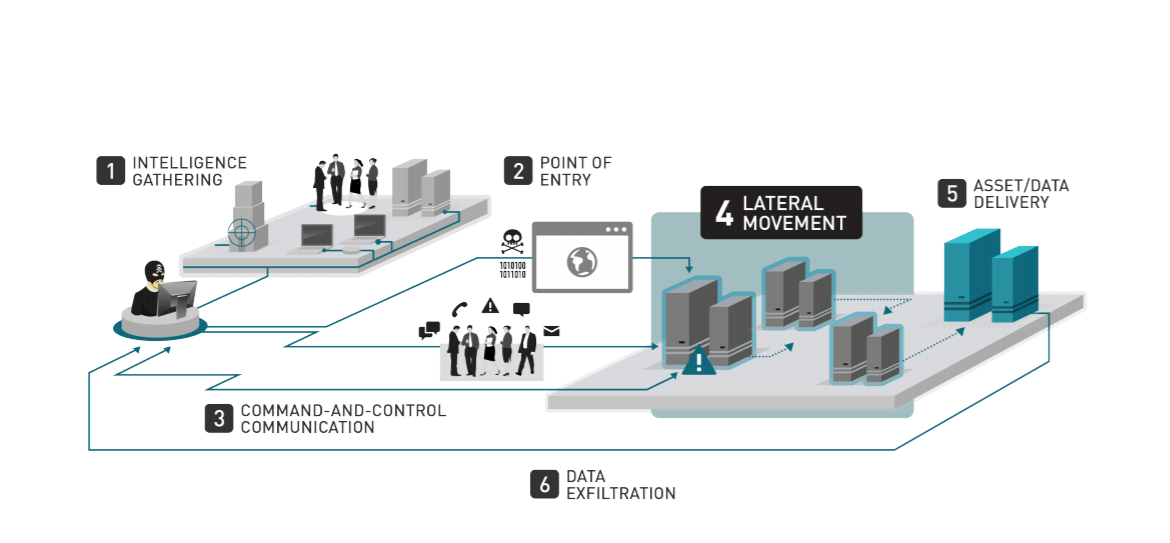

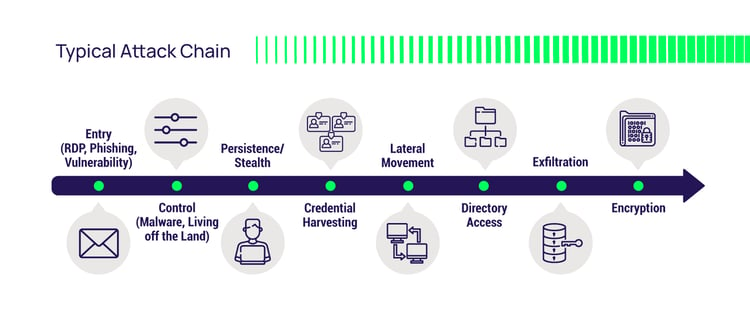
-1.webp)






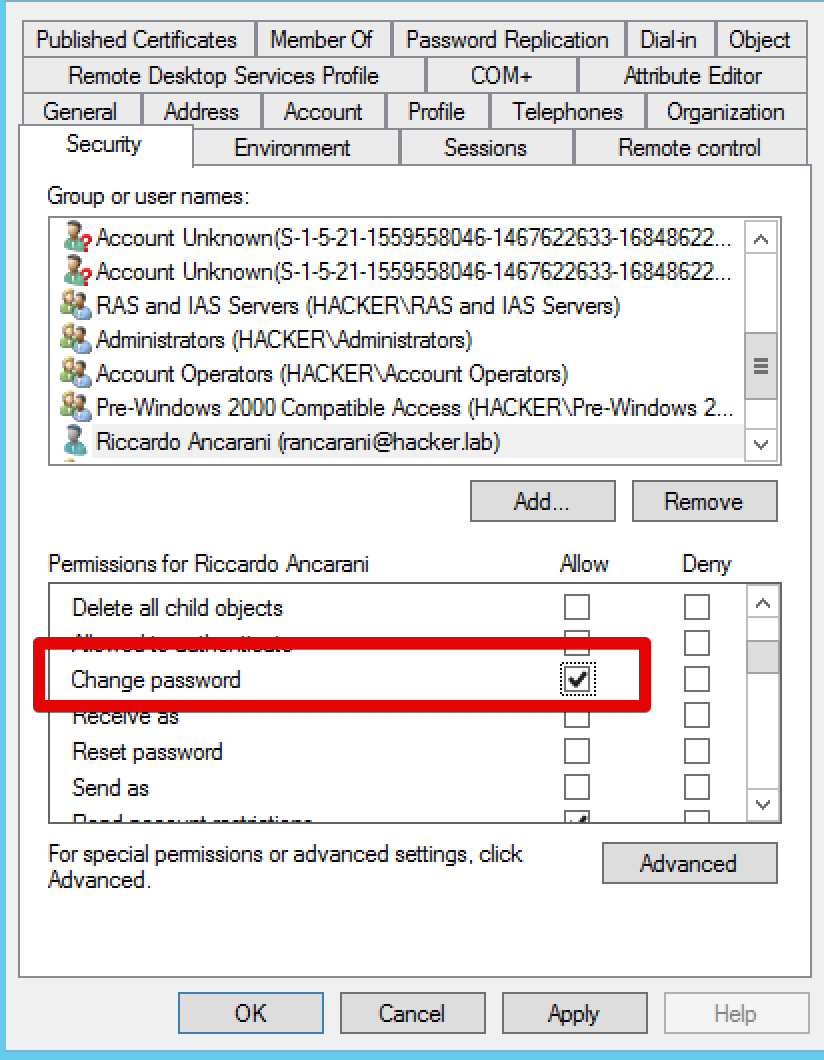

![Lateral Movement - Part 1 [Active Directory Hacking] -- TryHackMe LIVE! - YouTube Lateral Movement - Part 1 [Active Directory Hacking] -- TryHackMe LIVE! - YouTube](https://i.ytimg.com/vi/basSfhSJW0Y/maxresdefault.jpg)

